Why use Enkrypted Chat?
Explore below for more information on why Enkrypted Chat is secure and simple.
Share Securely
Advanced end-to-end encryption by our cascading cipher keeps your conversations secure. Only you and your peer can send/recieve messages or have calls.
Be Yourself
Send and recieve text, voice messages, photos, videos, GIFs and much more using your device's data connection
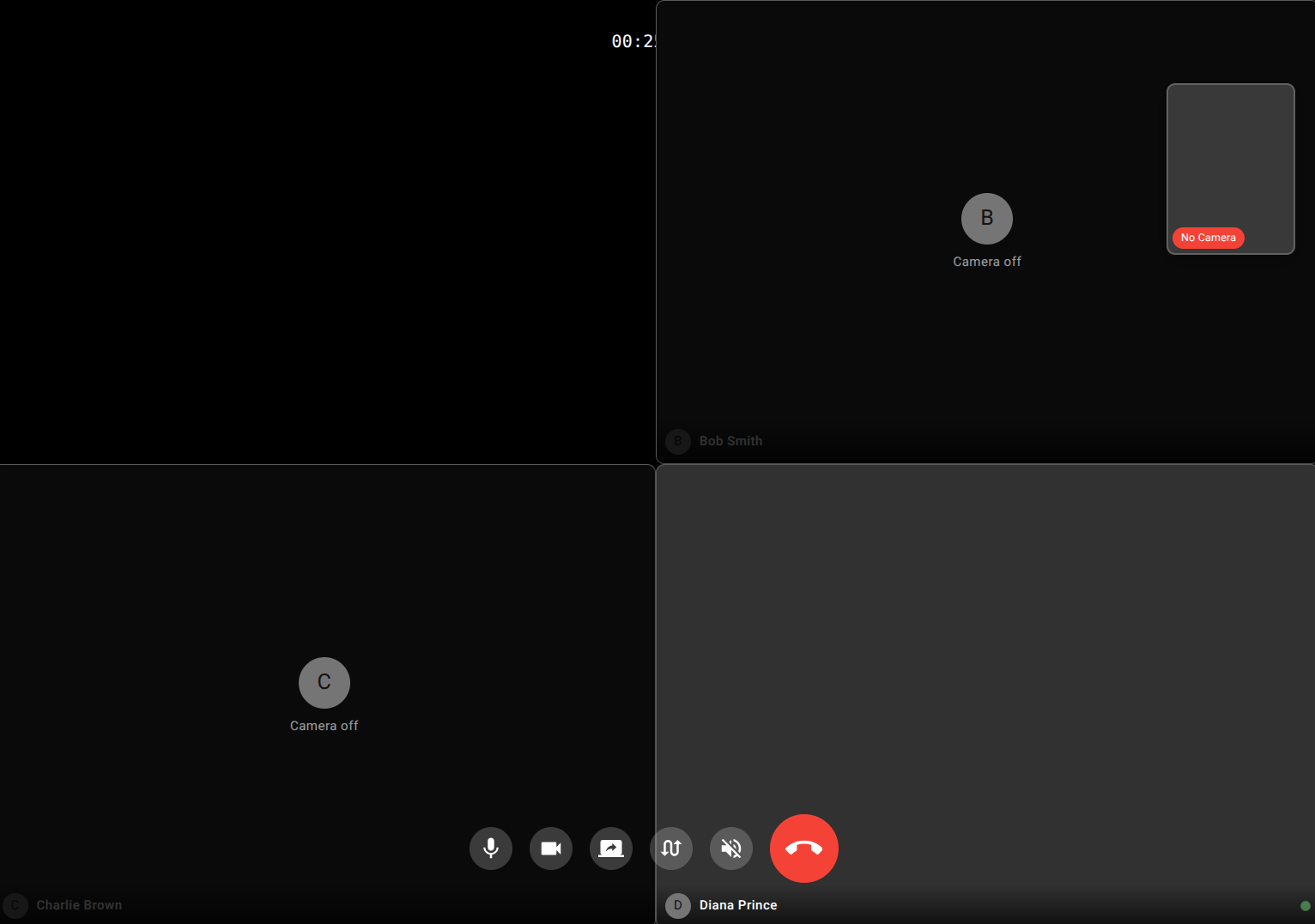
Express Yourself
Send and recieve crystal clear voice and video calls with your friends and family.
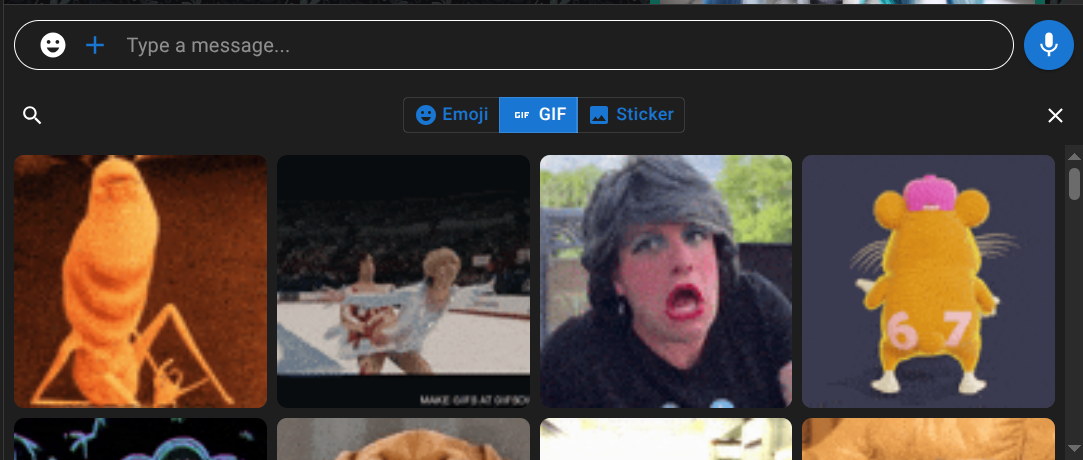
Have Fun
Use emojis, stickers, and GIFs to express yourself and show your friends how you feel.
No Installation. No Registration. No Tracking. No Limits.
There are no ads, no affiliate marketers and no tracking. You can use Enkrypted Chat without any real setup, so focus on the moments you want to share.

Research and Development
Innovating is a big part of what we do. We are always looking for new ways to improve the technology, user experience and the security of our products.
Sparcle
Experience Secure Messaging, Effortless File Sharing, and Crystal-clear Voice & Video Calls—all with cutting-edge P2P Technology.

Glitr.io
Using P2P E2EE file transfer, you have total privacy, seamless sharing. Connect Across all platforms. State-of-the-art encryption and universal file transfer.
P2P Call
Secure peer-to-peer video calls with end-to-end encryption. Connect directly with other users without routing through central servers.

File Vault
Browser-based file vault with robust encryption, on device storage. Bridging security and convenience for your sensitive data.

P2P Chat
Experience Secure Messaging, Effortless File Sharing, and Crystal-clear Voice & Video Calls—all with cutting-edge P2P Technology.
Free For Everyone
positive-intentions is an independent project and is not funded or monetized in any way. We are not selling your data or using it for any purpose. Please consider supporting us with a donation.
Support Us